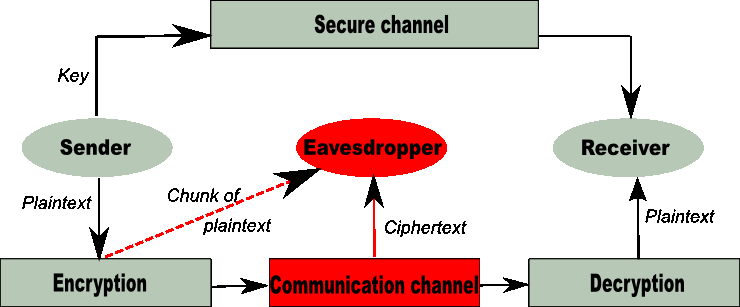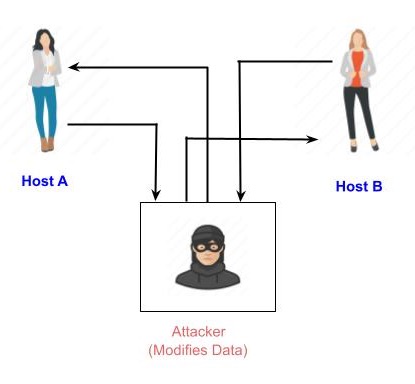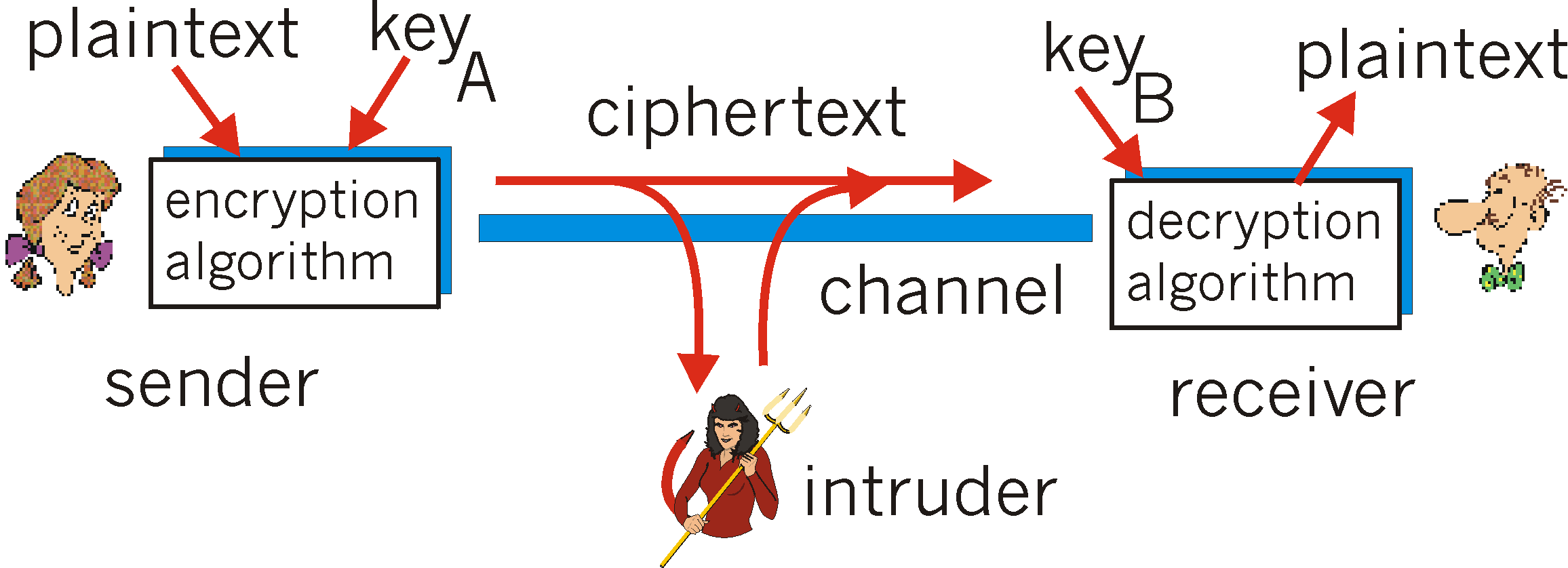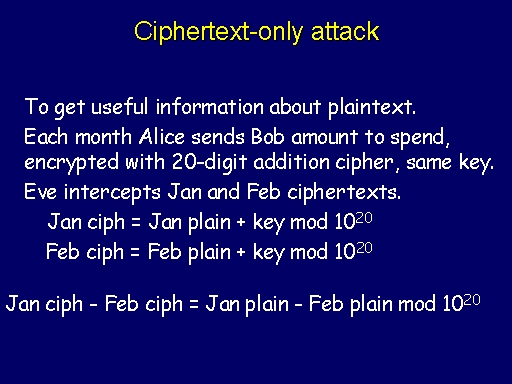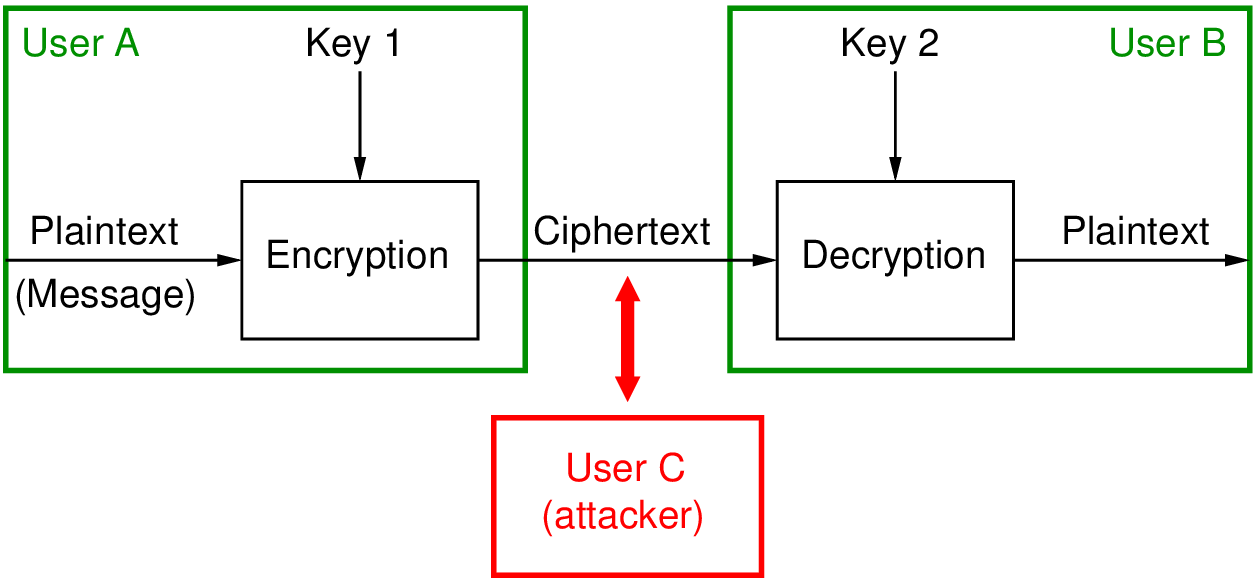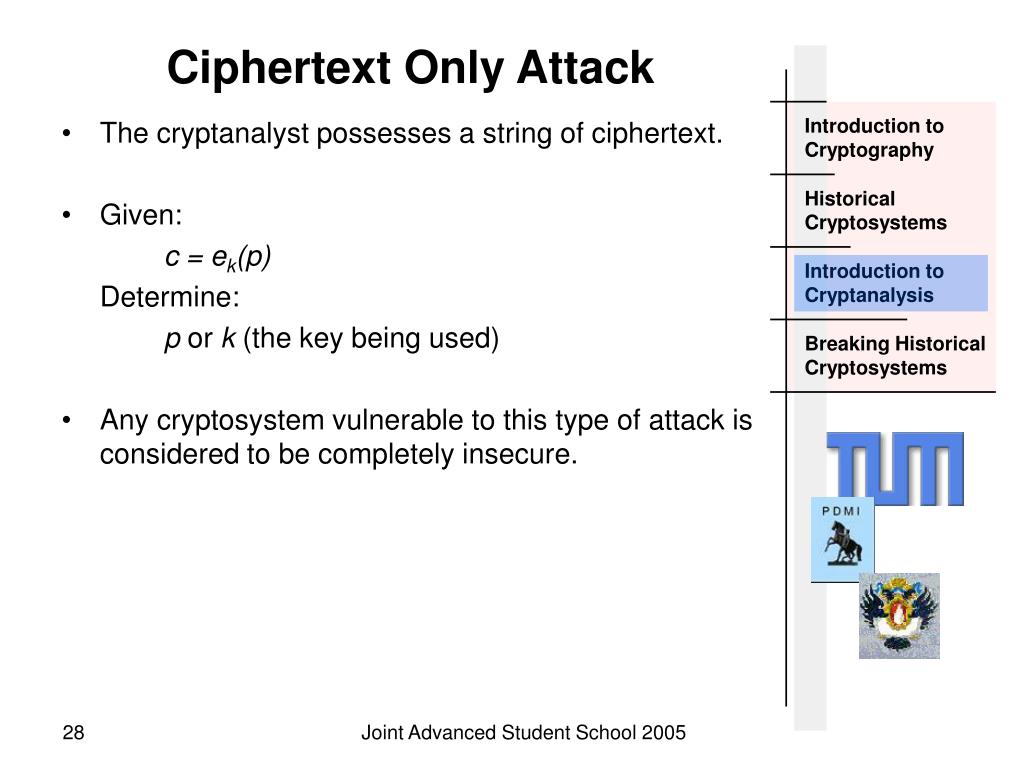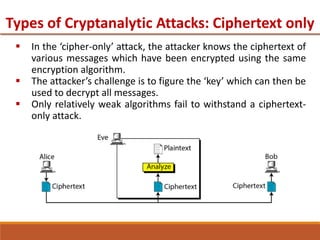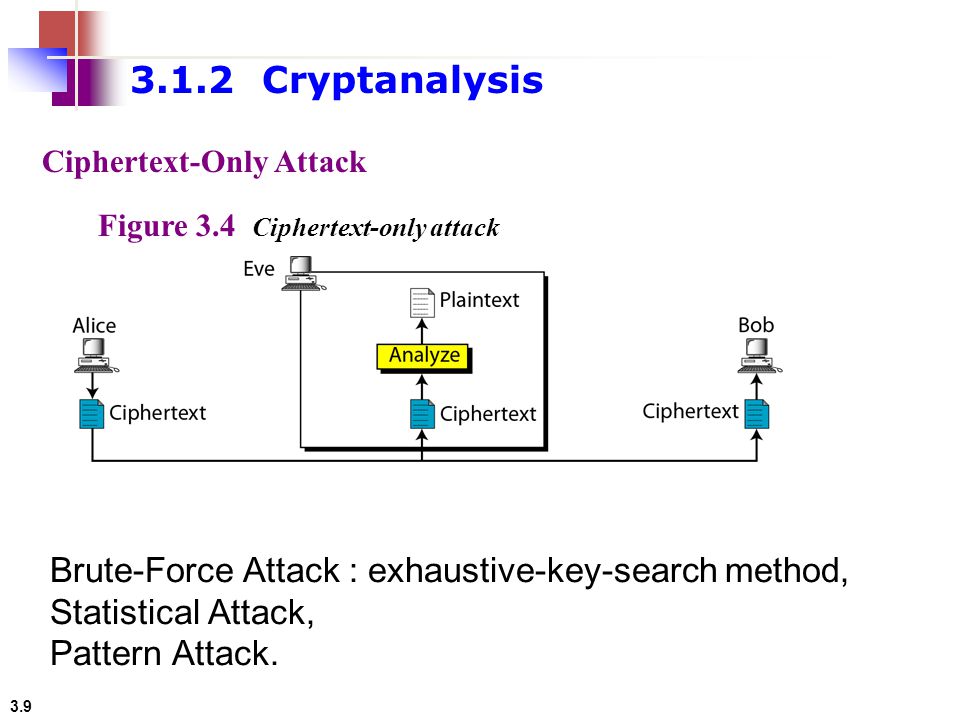
3.1 Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. Chapter 3 Traditional Symmetric-Key Ciphers. - ppt download
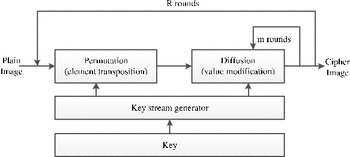
Chosen-plaintext attack of an image encryption scheme based on modified permutation–diffusion structure | SpringerLink

Known Plaintext attack vs Chosen plaintext attack - Blog on Information Security and other technical topics